
Hancitor's packer demystified
Post about reverse-engineering a packer which has been used in the past year by the Hancitor malware family to evade security detection. The packer can also be linked to many other financially motivated attacks in the past.

How TrickBot tricks its victims with webinjects
Blog which discusses how the TrickBot banking trojan uses webinjects to alter the contents of banking websites with the goal of defrauding its victims. The post also discusses how banks may detect customers infected by TrickBot.

Malicious dropper as an attack vector
Post which discusses different types of malicious droppers (file extensions) which may be used as an attack vector. These malicious droppers are often used in the weaponization phase of the cyber kill chain with the goal of compromising a system.

Booby trap a shortcut with a backdoor
Post which gives insight into how malware, which was allegedly used by the same group responsible for hacking the DNC and influencing the 2016 American elections, is built.

Inside the necurs botnet: the origin of locky malspam
Post which discusses methods to track the Necurs botnet: a centrally controlled group of computers on which a backdoor is installed. The article explains how a threat intelligence tool, which tracks the malicious mails sent by the botnet, can be built.
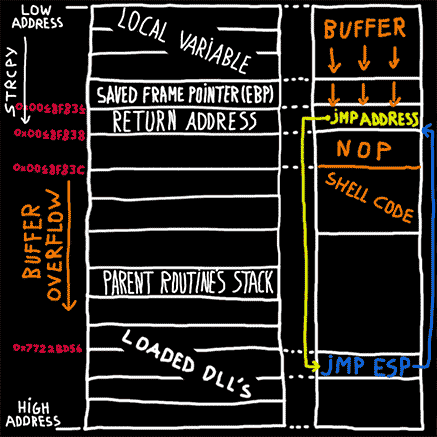
Buffer overflow explained
Post which discusses how arbitrary code execution in a program can be achieved by exploiting a buffer overflow vulnerability

Analyzing rig exploit kit
Post which discusses the Rig exploit kit: a kit used by cyber criminals to distribute malware. The kit abuses (exploits) flaws in outdated software in such a way that if a victim browses to a compromised site, its computer might get infected.
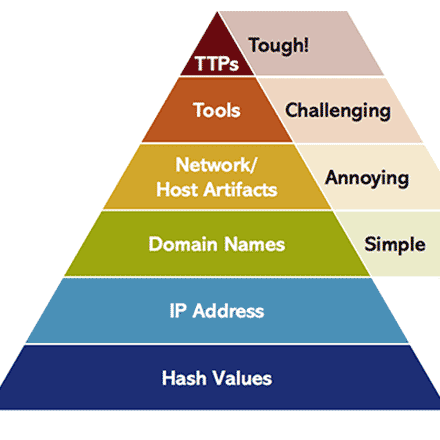
The pyramid of pain in threat hunting
Blog that discusses the theory of the pyramid of pain (the potential of threat intell) in threat hunting

Analyzing malicious office documents
Post which discusses weaponized office documents: documents, e.g. a word or excel document, with embedded malware. The post discusses three ways to spread malware via office documents: VBA macros, OLE objects and microsoft office exploits.
Analysis of a packed pony downloader
Malware reverse engineering tutorial which explains how self-defending malware making use of packers can be dissected.

Deobfuscating a Locky dropper
Tutorial which explains how an obfuscated javascript dropper (a javascript which needlessly contains complex constructs, in order to make it more difficult for antivirus software to detect the codes malicious nature) can be deobfuscated.
Analysis of an Angler Wordpress backdoor
Post which discusses how malicious code is injected in compromised websites. The malicious code redirects visitors of the compromised website to an exploit kit.
A closer look to fileless click fraud malware: Poweliks
Post which discusses the techniques used by Poweliks: malware which lives in the computers registry and which generates artificial traffic towards advertisement sites.
Reverse engineering Tinder: retrieving privacy-sensitive data
Post which discusses hunting for (security) vulnerabilities in Tinder. The post discusses a sensitive data exposure vulnerability in Tinder, which got fixed by Tinder within forty-eight hours.

Dridex: a modern bank robber
Post which discusses the Dridex banking trojan: a virus which is able to steal information submitted to an online banking application. The stolen information (such as authentication codes) is used to defraud the victim at a later stage.
Top three interesting facts about Angler exploit kit
Post which discusses the Angler exploit kit: a kit used by cyber criminals to distribute malware. The kit abuses (exploits) flaws in outdated software in such a way that if a victim browses to a compromised site, its computer might get infected.
Pretty Good Privacy (PGP) explained
Article which explains PGP: an asymmetric encryption algorithm used to digitally sign a message or to encode a message in such a way that only the intended receiver is able to decode the message.
